Device configuration
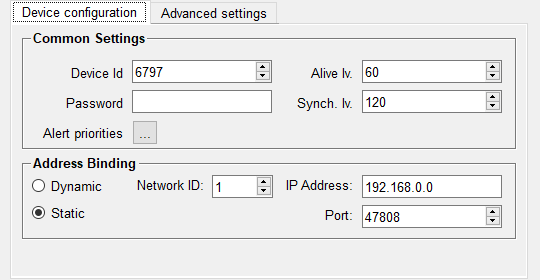
Common Settings
Enter in the Device Id input field the unique identification number for the BACnet device or use the spin buttons to do so.
Enter in the Password input field an individual password for the BACnet device configuration. This password will be used for the BACnet services (e.g. "DeviceCommunicationControl" and "ReInitializeDevice" - re-initialization of the device). If a password will not be defined, so the password will not be sent to the BACnet device.
Enter in the Alive Iv. input field the time in seconds after whose expiration an alive check for this device should be performed in the network. The default value is 0, whereby the interval is adopted from the deviceStatusPollTimeout config entry (if this config entry is not set, the general default value is 30 seconds). If the alive interval is set to greater than 0 seconds, then the interval is used (only) for this device (per BACnet device configurable). The alive check is carried out using a ReadProperty request.
If the time for the alive check is to high, it may happen that a connection loss will not be recognized early enough what leads to the fact that alarms get lost. This can be avoided by periodical triggering of GetEventInformation (e.g. by a script).
Enter in the Synch Iv. input field the time in seconds, after which an automatic time synchronization of the device is performed. Therefore a static Address Binding must be defined (see further below) in order to trigger a time synchronization directed to the device with the specified IP address. The default value is 0, whereby no directed time synchronization is triggered. A manual time synchronization can be performed using the Time command from the configuration panel. It is only supported for static bindings.
A time synchronization via broadcast to all BACnet devices in the network can be triggered with the internal data point element _Bacnet_x.Command.SyncTime.
If the BACnet driver can not connect to the utcTimeSynchronization service, the internal synchronization of WinCC OA is used as fallback.
Click the "..." button next to Alert priorities to map BACnet priorities to WinCC OA alert classes for the selected device in the Alert Priority Mapping panel. This is only necessary if a different mapping should be defined for various devices, else it is possible to carry out the mapping for a selected internal BACnet driver data point (is valid for all devices), see Alarm priority mapping. As both panels have the same layout, please follow the configuration instructions described there.
A configured alert priority mapping for a BACnet device is used always preferentially than the mapping for a BACnet driver. Otherwise the mapping defined in the driver is used.
Address Binding
There are two possibilities to set the BACnet/IP address for a device - dynamic or static.
If dynamic is chosen, the address is assigned dynamically. This means that the driver determines the BACnet/IP address from the "I am" telegrams of the BACnet devices.
If in the time between the BACnet device has sent the "I am" message and the update of the Address Binding a command is triggered, this possibly can get lost, as it was sent to the device with the old IP address.
If an IP address of a BACnet device changes and the BACnet driver is started afterwards, the Address Binding is updated automatically, since the BACnet driver triggers a "Who Is" message using the "DM-DDB-A" BIBB and receives the corresponding "I am" messages with the new information.
If static is chosen, the BACnet/IP address has to be allocated by the user - thus, an automatic update is not performed. If there is a change in the information, this has to be updated manually by the user.
The information is:
-
Network ID - Here, enter the number of the network ID the device resides (max. 65535).
-
Port - Here, enter the UDP port for the communication to the BACnet device.
-
IP-Address - Here, enter the IP address of the BACnet device.
If the same IP address or Device Id is used twice, only one connection can be established, i.e. a flawless operation can not be assured. This also applies to inactive configurations.



