IEC 61850 Control Model
Overview
For sending a critical command to a protection device you have to perform specific operations which are defined by the control model. The definitions include:
-
Operations at different levels of security
-
The services required to perform these operations
-
The data structures for handling and monitoring the service requests
The target of an operation is the controllable object, e.g. the position of switch with all its defining attributes.
It is not possible to change the position of a switch on a protection device by just writing the desired value.
Operations
For writing commands to a peripheral device the IEC 61850 standard defines the following operations:
-
Control with normal security
-
-
Direct control with normal security
-
Select before operate (SBO) control with normal security
-
-
Control with enhanced security
-
-
Direct control with enhanced security
-
Select before operate (SBO) control with enhanced security
-
Direct control provides a simple way to initiate an action at device level without checking the safety aspects. It can be used for controlling a local object at device level or an external object where the supervision information is not critical at the client end. This model cannot prevent conflicting situations that can occur if control data is written from multiple clients simultaneously.
Control with normal security
The status of the controllable object is not supervised. This means, that the client is not notified if the operation was performed successfully or failed.
Direct control with normal security
Allows the services Operate, TimeActivatedOperate and Cancel. A command can be written immediately by calling the services Operate or TimeActivatedOperate.
Select before operate with normal security
Allows the services Select, Operate, TimeActivatedOperate and Cancel. Before a command can be written the controllable object must be selected by using the Select service.
Control with enhanced security
When using enhanced security the status of the operation is supervised and the peripheral device provides detailed information in case of failure.
Direct control with enhanced security
Allows the services Operate, TimeActivatedOperate and Cancel. A command can be written immediately by calling the services Operate or TimeActivatedOperate.
Select before operate with enhanced security
Allows the services SelectWithValue, Operate, TimeActivatedOperate and Cancel. Before a command can be written the controllable object must be selected by using the SelectWithValue service.
Services
To perform the operations the following services are introduced:
Operate
Is used to send a command, e.g. to change the position of a switch on the peripheral device.
TimeActivatedOperate
Is used to perform a command at a defined time.
Cancel
Is used to terminate a command before it is executed.
Select
Is used to select a controllable object before operating it. The operation must be performed within the time span defined by the attribute sboTimeout. For this time span the object is exclusively reserved for the client that has selected it. The object is released when the time-out expires or by command termination.
SelectWithValue
Provides the same functionality as Select but requires sending the controlling value together with the Select request.
Data Structures
The IEC standard defines the following data structures for operating and supervising controllable objects:
Oper and SBOw structure
These structures are used to call the services Operate, TimeActivatedOperate, Select and SelectWithValue.
| Elements | WinCC OA transformation type |
|---|---|
| ctlVal | Depends on the CDC type |
| operTm | TIMESTAMP |
| origin.Orcat | INT32 |
| origin.orIdent | OCTET STRING64 |
| ctlNum | INT8U |
| T | TIMESTAMP |
| Test | BOOLEAN |
| Check | BITSTRING |
Cancel structure
This structure is used to call the Cancel service.
| Elements | WinCC OA transformation type |
|---|---|
| ctlVal | Depends on the CDC type |
| operTm | TIMESTAMP |
| origin.Orcat | INT32 |
| origin.orIdent | OCTET STRING64 |
| ctlNum | INT8U |
| T | TIMESTAMP |
| Test | BOOLEAN |
These data structures are of functional constraint CO (Controllable). In a device they would be structured as in the following figure.
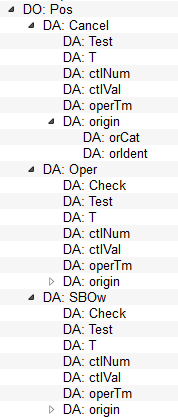
Controllable Object Service Parameters
ctlVal
The service parameter ctlVal (control value) determines the control activity. The type ctlVal matches the type of the controlled attribute defined in the common data class of the controllable object.
operTm
If a TimeActivatedOperate service is run, the service parameter operTm specifies the time when the command will be executed. The service parameter operTm is optional and not supported by all devices.
origin
The service parameter origin determines the originator of the control service. All service requests belonging to one control sequence must be identified by the same originator.
origin.orCat
The originator category specifies the category of the originator. E.g. station control (2) is used if a control operation issued from an operator using a client location at the station level. Automatic station (5) is used if a control operation is used from an automatic function at the station level.
| Value | Meaning |
|---|---|
| 0 | Not supported |
| 1 | bay-control |
| 2 | station-control |
| 3 | remote-control |
| 4 | automatic-bay |
| 5 | automatic-station |
| 6 | automatic-remote |
| 7 | maintenance |
| 8 | process |
To distinguish between the operation levels (bay, station or remote) the config entry originatorCategory is used.
To distinguish between commands issued by the operator and the application the Bit6 of the CommandByte is used. If this bit is set, the command is defined as automatic.
Example
The config entry originatorCategory is set to 3.
-
Bit 6 is not set: The originator category is defined as "remote control"
-
Bit 6 is set: The originator category is defined as "automatic-remote".
origin.orIdent
The originator identification shows the identification of the peer sending the object (request or answer). The value NULL indicates that the originator of a particular object is not known.
By default the original identifier is defined as <hostname>_<project name>_<driver number>. The host name can be defined by using the config entry originatorIdentifier.
 Example
Example
A WinCC OA project "IEC61850TestProject" is running on the host "MyETMHost" with driver number 1 assigned to the WinCC OA 61850/61400 client.
By default the originator identifier is constructed as "MyETMHost_IEC61850TestProject_1". By setting the config entry originatorIdentifier = "SubstationTestHost" the originator identifier will become "SubstationTestHost_IEC61850TestProject_1".
ctlNum
The service parameter ctlNum determines the control sequence number of the control service. All service requests belonging to one control sequence must be identified by the same control sequence number. The control sequence number is assigned by the client, the value may range from 0 to 255.
T
The service parameter T is the time stamp of the control object. It contains the time when the client issues the service control request.
Test
The service parameter Test indicates if the client sends a control service for test purposes only. True indicates test.
All service requests belonging to one control sequence must carry the same test status.
Check
The service parameter Check specifies the kind of checks a control object shall perform before issuing the control operation, if the common data class is DPC (double point control). If the service parameter Check is not supported by the data object it will be ignored and the request will be handled.



