Config Entries for SSA for Managers
In the server-side authentication (SSA) for managers the managers must authenticate themselves by using certificates. This chapter contains the config entries that are required to use certificates in a WinCC OA SSA for Managers project.
Note that you have to create your own certificates and configure the server-side authentication for managers before setting the config entries.
SSL Communication with filebased Certificates
| Config entry | Description |
|---|---|
|
[general] accessControlPlugin ="AccessControlPlugin" |
Server-side Authentication for Managers: [general] accessControlPlugin = "AccessControlPlugin" Loads the accessControlPlugin. and activates the servers-side authentication for managers, see Server-side Authentication for Managers, Basics.) Server-side Authentication for UI Managers: When you use the server-side authentication for UI Managers, use the following config entry [general] accessControlPlugin = "AccessControlPluginUser" It activates the server-side authentication for UI managers. |
|
[webClient] clientSideAuth = 0 httpsPort = 443 httpPort = 0 rootPanel = "vision/login.pnl" mobileRootPanel = "vision/login.pnl" |
The entry clientSideAuth activates the server-side authentication. Furthermore, you need the "accessControlPlugin" config entry, see above. With the httpsPort you specify the default port for an HTTPS connection and via the httpPort entry you set the HTTP port to 0. The httpPort is disabled. To specify a start panel when the UI is started, use either the rootPanel entry for UI: [webClient] rootPanel = "vision/login.pnl" or the mobileRootPanel entry for the mobile UI application: [webClient] mobileRootPanel = "vision/login.pnl" If these config entries are not set, the login.pnl is shown since it is the default. You can specify your own panel, otherwise the default is shown. |
|
[ui] httpServer = "https://localhost:443" |
Specify the WebServer and the port number. |
|
ROOT CERTIFICATE: [general] ssaChainFile = "root-cert.pem" HOST KEY AND HOST CERTIFICATE: [general] ssaPrivateKey = "file:hostUserName.key" ssaCertificate = "file:hostUserName.crt" Also certificates and keys with the extension .pem can be used: ssaCertificate = "file:hostUserName.cert.pem" ssaPrivateKey = "file:hostUserName.key.pem" |
ROOT CERTIFICATE:
HOST KEY AND HOST CERTIFICATE:
file: the prefix specifies that the key and the certificate are loaded from a file. |
|
[httpServer] uiArguments = "-p vision/login.pnl -centered -iconBar -menuBar -ssa" |
Activate the server-side authentication of the ULC UX by adding the config entry uiArguments to the config file of your server project. |
For an example of the server-side authentication for Managers, see chapter Example Configuration - SSA for Managers.
SSL Communication with Windows Certificate Store certificates:
| Config entry | Description |
|---|---|
|
[general] accessControlPlugin = "AccessControlPlugin" ssaCertCheck ="chainPrefix=root_SSA" |
Loads the accessControlPlugin. See Server-side Authentication for UI Managers, Basics). When you use the server-side authentication for UI Managers, use the config entry [general] accessControlPlugin = "AccessControlPluginUser" With the entry "ssaCertCheck", the required name for a certificate chain is defined, thus a host certificate is recognized as valid. In this case the name "root_SSA" should appear in the certificate. If there is an intermediate CA, a possible entry is as follows: ssaCertCheck = "chainPrefix=myETM_RootCA;myETM_IntermediateCA" In this case there is a root CA with the common name "myETM_RootCA" and an intermediate with myETM_IntermediateCA". When assigning this entry, all characters from the config entry must appear in the certificate. As an example, if e.g. the entry was set as follows: "ssaCertCheck = "chainPrefix=my" everything that begins with "my" is valid. So this is not only valid for myETM..., but also, for example, for "mySiemens..." etc. |
|
[webClient] clientSideAuth = 0 |
Activates the server-side authentication. |
|
[ui] httpServer = "https://localhost:443" |
Specifies the WebServer and the port number. |
|
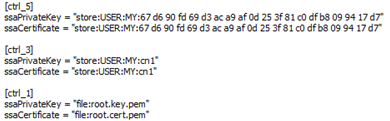
[general]
ssaPrivateKey = "store:USER:MY:67 d6 90 fd 69 d3 ac a9 af 0d 25 3f 81 c0 df b8 09 94 17 d7" ssaCertificate = "store:USER:MY:67 d6 90 fd 69 d3 ac a9 af 0d 25 3f 81 c0 df b8 09 94 17 d7"
ssaPrivateKey = "store:USER:MY:cn1" ssaCertificate = "store:USER:MY:cn1" |
The entries specify which certificates are searched in the Windows Certificate Store. Here (see the figure on the left), certificates are searched via thumbprint. When these config entries are set in the [general] section of the config file, the config entry sslChainFile may not be set since the certificates would not be searched in the Windows Cert Store. Here (see figure on the left) certificates are searched via the name. There are two areas for the Certificate Store in Windows: 1 - machine 2 - user If a certificate is imported into the machine, this certificate is available for all users of this machine - we recommend this setting. In this case the config entry begins with "store: MACHINE: ..." In the case described with "store: USER: ...", the certificates are only available for a specific user. This distinction must be made in the config entry so that the correct store is searched for. |
|
If the config entries ssaPrivateKey and ssaCertificate are set for different managers, these managers use different certificates and keys than in the [general] section. |
For an example of config files for SSA for Managers, see chapter Create, Covert and Import SSA Certificates.





