OPC UA Certificates
A certificate is a digitally signed data structure that describes capabilities of a Client or Server. Both the WinCC OA client and server is delivered with default certificates, which can be changed by configuration. The default certificates are self signed certificates. You must replace the default certificates with your own certificates.
To use another than the default certificate, you have to define it via serverCertificate config entry in the [opcuasrv] section. The certificate for the UA client can be defined via the Client Certificate field (see Configuration of the Servers).
The OPC UA certificate handling allows
-
Defining which certificates are accepted on the server or for the client (see "Accept Certificates").
-
Creating new client/server certificates (see "Create Certificate").
Open the certificate handling via a click on the OPC UA Certificate in the Driver tab of the system management.
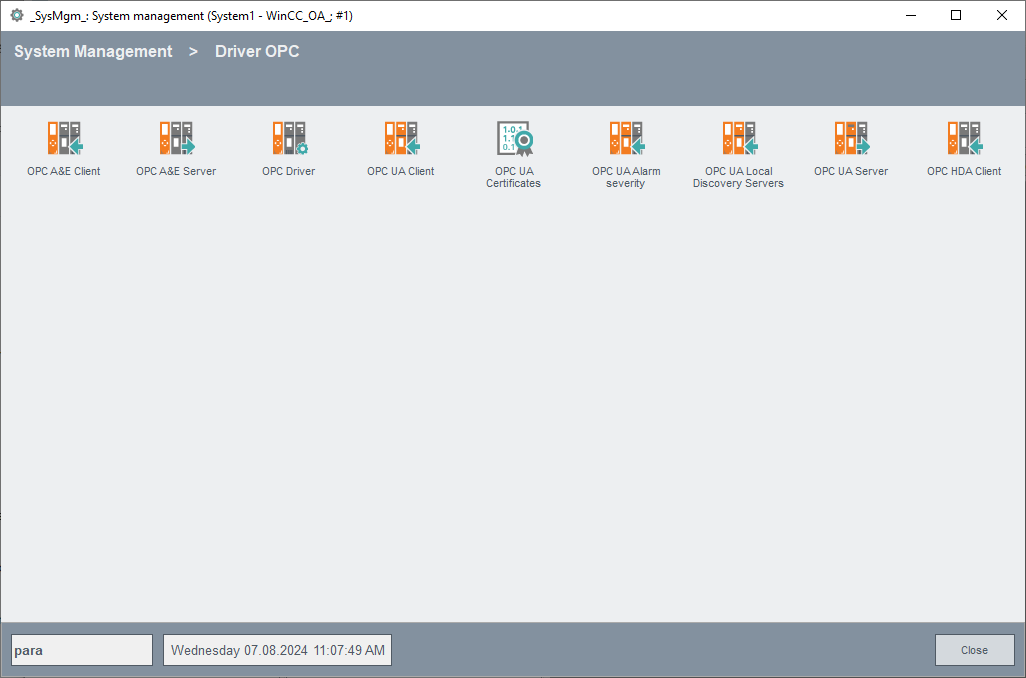
OPC UA specific certificate handling
The OPC UA certificates require the certifiate field SubjectAlternativeName for application URI and host name or IP address information. For communication with security the OPC UA Server verifies if the application URI of the client is matching the application URI of the client certificate. The application URI of the client can be configured with the UA client config entry "applicationUri".
On the other hand in the secure communication case the client verifies that the UA server host name or IP address in the server URL is matching the server DNS name or IP address in the server certificate. This check is only done if the server URL has an host name or IP address different to "localhost". This check can be deactivated with UA client config entry "checkCertificateHost".
If you use the default certificate for the server, the host name cannot be correct. In this case the check on client side must be deactivated..
Accept Certificates
On the server it is possible to decide whether a client certificate should be accepted or not. For the client it is possible to decide whether a server certificate should be accepted or not. To switch between client and server you can use the Certificates for combo box.
From technical point of view a certificate, which should be accepted, is moved from the "rejected" directory to the "certs" directory. For the meaning of the specific directories see Management and Formats.
ETM certificates for client and server are delivered with WinCC OA:
- PVSS_UA_defaultclient.der, PVSS_UA_server.der,
PVSS_UA_server.pemPVSS_UA_defaultclient.pem;- Version 3.11 and greater: WinCC_OA_UA_Client.der,
WinCC_OA_UA_Server.der, WinCC_OA_UA_server.pem and
WinCC_OA_UA_Client.pem.These can be found in the WinCC OA installation directory under
\data\opcua\client\PKI\CA\ in the corresponding directories
(see Management and Formats).
Figure: "Accept Certificates" tab
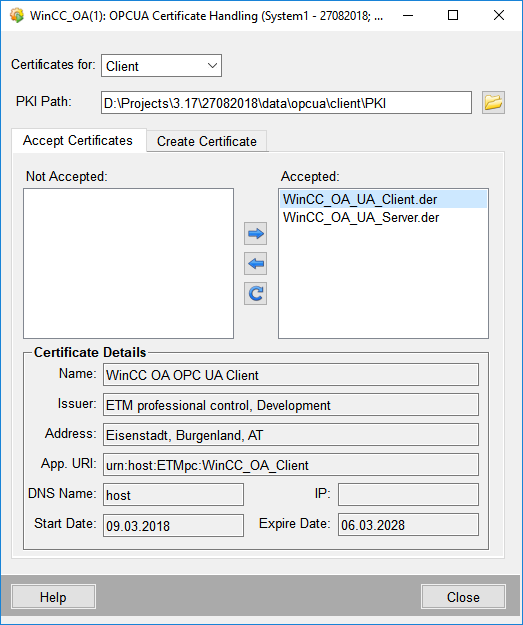
In the list on the left all certificates are shown, which are not accepted. These can be found in the "rejected" directory.
In the list on the right all certificates are shown, which are accepted. These can be found in the "certs" directory.
For moving the certificates from one list (or directory) to the other, select the
specific certificate and use the buttons ![]() (reject certificate) and
(reject certificate) and ![]() (accept certificate) to move it.
(accept certificate) to move it.
When a certificate is moved from the "Accepted" list to the "Not Accepted" list, the client does not reject the server immediately if the connection is already active. After a reconnect, the client will reject the not accepted server.
If a certificate is selected from one of the two lists, the certificate details are displayed in the bottom of the panel ("Certificate Details").
The client and the server check the certificates of their partners and store them in an separate "rejected" directory, if they are unknown. For example if the client does not know the server, this stores a certificate file in the client/PKI/CA/rejected directory.
As well as for the client as for the server the location of the certificate directory can be changed with the certificateStore config entry.
Both client and server must have write rights to the "rejected" directory. The user interface needs an additional write right in the "certs" directory in order to accept certificates.
In the scope of the SecureChannel services, certificates will also be exchanged, when the security setting is set to None. This means, a certificate is always exchanged, even if the user is working without a security setting.
However, a validation of the certificates does not take place. This procedure is carried out automatically by the communication stack or SDK.
Create Client / Server Certificate
The WinCC OA panel for certificate handling provides the creation of self signed client /server certificates. Thereby only selective clients can access the server.
If certificates are created by a CA (Certificate Authority), typically an IT administrator, these must have the preset file extensions/formats according to the OPC UA specification.
Self signed certificates contain the parameters shown in the figure below (example of a configuration).
Please note that:
-
All input fields must be filled.
-
The certificate name has to be entered without file extension.
-
The certificate name may not contain blanks and/or special characters (/ \ ; ? < > * | : " ').
Click on "Create Certificate" to create it. The certificate is stored in the data\opcua\client\PKI\CA\certs directory and thus it is accepted automatically.
In order to delete a certificate this must be deleted manually from the corresponding directory.
You have to switch to the correct directory before creating certificates. Per default the client directory is selected when opening the panel.
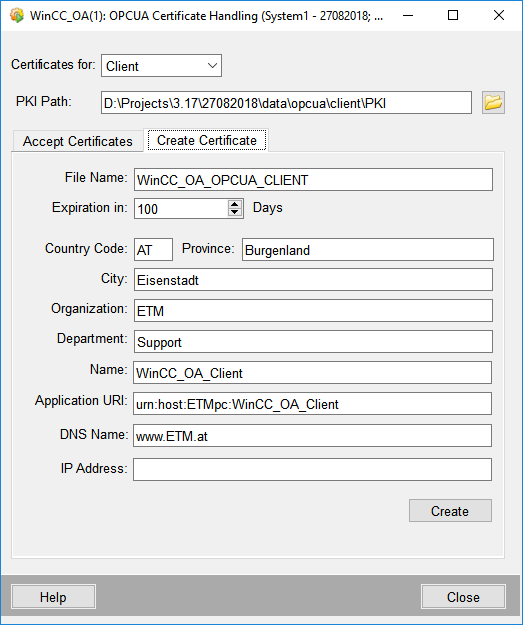
File Name
The file name of the certificate. The name must be entered without a file extension.
Expiration in
Certificate expiration date in days.
Country code
A two letter country code, e.g. AT for Austria.
Province, City, Organization, Department
Specific information on location, company etc.
Name
The name of the application, e.g. WinCC OA client.
Application URI
Uniform Resource Identifier for the application. In case of a server certificate the following format is necessary:
urn:<Server DNS name>:WinCC_OA:<WinCC OA project name>:<OPC UA server number>
Server DNS name must be the same as specified in the DNS Name field. For the WinCC OA project name the project in which the OPC UA server is running must be defined. The OPC UA server number is equal to the manager number of the OPC UA server.
DNS Name
The host name. Multiple host names can be entered separated by spaces.
IP Address
Multiple IP addresses can be entered separated by spaces.
Management and Formats
A directory for certificates is necessary for UA server and client. The directories for server and client can be defined via the certificateStore config entry. The structure of the directories is preset as described below.
Per default the UA server looks for its PKI certificate directory under <WinCC_OA_Proj>/data/opcua/server, the client under <WinCC_OA_Proj>/data/opcua/client. If the respective directory does not exist, potential sub projects and the installation directory are browsed.
With 3.15 P008 the certificate directories of client and server are automatically copied from the installation directory to the respective project when creating a new project. This means that created certificates or rejected certificates from communication partners are stored in the project directory per default.
Server
| Directory | Description |
| certs | Certificates of the UA server and certificates of trusted clients or certification authorities (CA) are stored here. These files with .der extension are X.509 certificates, which contain the public key. |
| clr |
Certificate revocation lists of a CA are stored here. Example: All certificates of the CA xyz should be accepted except these from this directory. |
| private | Here the files with the .pem extension are stored. These files are X.509 certificates, which contain the public key, and have to be accessible only for authorized users on the file level (the IT administrator defines the corresponding access rights). |
| rejected | Al rejected certificates of communication partners are stored here. By copying these certificates to the certs directory on the file level these certificates can be applied to the list of trusted certificates. These files should be accessible only for authorized users. |
In the mentioned directories the certificates of the WinCC OA server (directory certs), trusted clients (certs) and rejected clients (rejected) are stored.
Client
Meaning and content of the directories are analogous to the server.
Using certificates from a Certificate Authority
The WinCC OA client and server can also use certificates signed by a Certificate Authority, i.e. no self signed certificates. Several aspects must be considered when using such certificates, because OPC UA requires some specific fields which are also checked. If the check fails no secure communication is possible.
For a detailed description on certificate content and processing please refer to chapter 6.2 in part 6 (Mappings) of the OPC UA specification. Chapter 6.1 in part 4 (Services) of the specification describes the certificates checks which are executed on client and server side.
There might be several reasons if the establishment of secure communication fails.
- The certificate is not in the trusted list. In that case trust the certificate, if trustable.
- Certificate host name validation on client side fails. In that case the host name or IP address in the server URL does not match the DNS name or IP in the server certificate. Either the server certificate must be corrected or the check on client side must be skipped using the checkCertificateHost config entry.
- Application URI verification at server side fails. In that case the application URI in the client certificate does not match the application URI the client uses. The application URI of the client can be configured with the config entry applicationUri.
- The Certificate Revocation List file is in PEM format but has the wrong file extension CRL. The file name must be changed to the correct extension.



