Secure Authentication
The WinCC OA DNP3 driver supports Secure Authentication (SA) version 5 as defined in IEEE Standard. 1815-2012 section 7. This allows a device to request authentication for critical operations. What a critical operation is, is up to the device configuration and cannot be defined by the DNP3 driver. If the driver is executing a critical operation (e.g. send a binary command), the device requests authentication. If the driver can successfully authenticate, the operation is executed. Otherwise it is rejected.
Secure Authentication - DNP3 Device Configuration

Depending on the WinCC OA Secure Authentication - DNP3 Driver Configuration, configure the device. Note the following:
WinCC OA Secure Authentication - DNP3 Driver Configuration
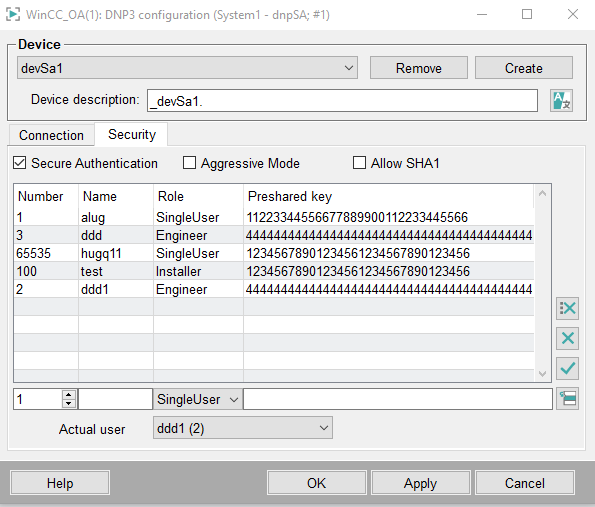
On the Security tab configure the Secure Authentication parameters:
Secure Authentication: Use this check box to enable the authentication. If the Secure Authentication is disabled, the connection does not use Secure Authentication.
Aggressive Mode: This option is used to activate the aggressive mode. This is a mode where no separate authentication challenge and reply is required. This means that the processing of critical operations is speed up since the authentication is part of a telegram and not a separate step. Aggressive mode must be only activated if it is supported by the device. If the device does not support this mode, Allow SHA1.
Since SHA1 is considered as unsafe, it is not enabled by default. However, devices that do not support more recent MAC algorithms might still be used. Therefore, this option is available.
You can specify a list of users with different roles and keys for each device. A device can support multiple users or not.
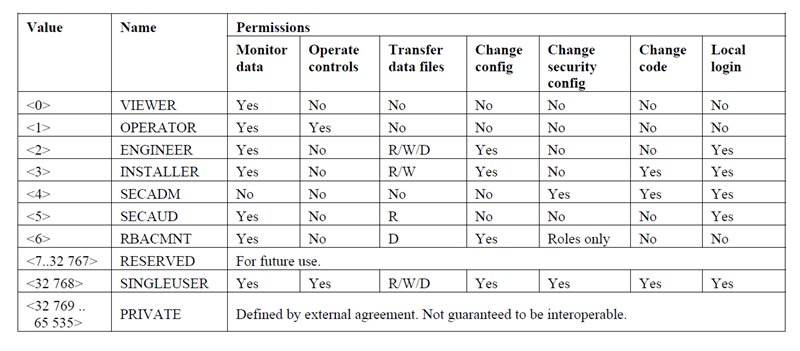
Depending on a role, the user has specific rights. The user can, for example, only view or also edit configurations.
Secure Authentication - DNP3 Statistics
You can read Security Statistics from a device that supports it. The device provides the statistics and WinCC OA DNP3 driver can read them, for example, "How often did the authentication fail"? The DNP3 Specification contains a whole list of Security Statistics. In order to query the statistics, you must add a periphery address to the group 121. The Variation for an address in group 121 must be 1.
The statistics are specified in the norm IEEE Std. 1815-2012 in the section 7.5.2.2.. Specify what you read by using the index of a security statistics object (of the Security Statistics group). Use, for example, index 12 meaning Successful Authentications in the address panel.