Basic Terms
What is a Certificate?
A PKI ( public-key infrastructure) certificate proves the ownership of a public key. SSL certificates have a key pair: public and private key. These are used to establish an encrypted connection.
-
information about key
-
information about the owner such as domain name, company name and location. The owner is called subject. The owner (subject) of a certificate can be a person or an organization but also a computer or a device.
and
-
the digital root signature of the issuer CA (certificate authority) that verified the content of the certificate.
What is a CA?
In a PKI, the certificate issuer is a CA.
Typically this is a company that issues certificates for customers and charges them.
CA signs certificates. CA processes the requests from people or organizations.
CA verifies the identity of the person who requests to create a certificate and the information and then creates a certificate and signs it. To sign a certificate, a CA needs a root certificate and the corresponding private key.
CA also maintains the information if an issued certificate is valid and a list of certificates that have been revoked (e.g. key has been compromised).
| Internal CA | External CA |
|---|---|
| It causes internal administrative efforts to handle host certificates. (e.g., Import CA into Trusted Certification Authorities) | Control of CA itself is not possible. |
| No financial costs per certificate. | The financial cost of SSL certificates depends on the type and functionality of the certificate. |
| It causes administrative effort for internet-facing applications. External partners do not trust an internal CA. | Trusted by most browsers (e.g., VeriSign). |
| The asset owner is responsible for protecting CA. | The vendor of a CA is responsible for protecting its infrastructure. |
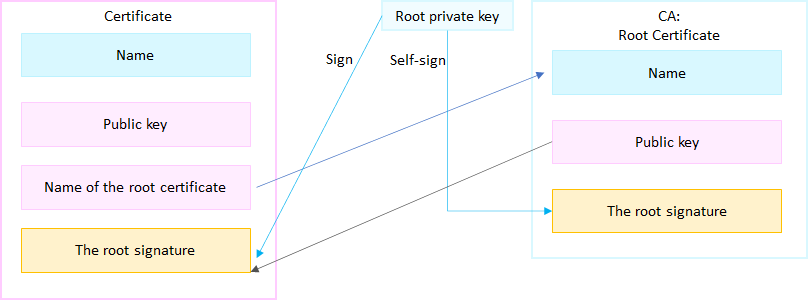
Public key: The public key is used together with the private key to establish an encrypted connection.
Name of the root certificate: To sign a certificate, a CA (certificate authority) needs a root certificate and the corresponding private key.
The root signature: CA verifies the identity of the person who requests to create a certificate and the information and then creates a certificate and signs it.