WinCC OA Internal Identity Provider
This topic provides an overview of the built-in OpenID Connect (OIDC) provider, its integration, configuration, and user management in WinCC OA projects.
An OpenID Connect (OIDC) based internal identity provider is a service that authenticates users and issues identity tokens. It enables single sign-on (SSO) and user identity management based on the OIDC protocol, which extends OAuth 2.0 with an identity layer.
WinCC OA includes a custom identity provider. This provider is integrated by default in all new projects of type OpenID Connect (OIDC) Project. The provider supports secure authentication and the user management is performed within the WinCC OA environment. The implementation supports the Proof Key for Code Exchange (PKCE) extension for enhanced security, and user authentication is performed using passwords.
The built-in identity provider is designed to offer an out-of-the-box identity provider solution, eliminating the need to configure a separate external service. It also serves as a local fallback for authentication, allowing users to log in if no other identity provider is accessible. The WinCC OA Internal Identity Provider functions solely as an identity provider (IdP) and does not act as a relying party (RP).
Integration
The OIDC provider is implemented in JavaScript and runs within a dedicated WinCC OA JavaScript Manager for Node.js. Leveraging Node.js
allows the provider to support modern authentication protocols and enables future
extensibility. This manager is automatically added and started by default in all new
OIDC projects, ensuring seamless integration with the WinCC OA
runtime environment. The provider manager is launched using the script
oa-identity-provider/oidc.cjs. The OIDC provider manager is
used when the authType is set to oidc in the
project configuration. For more information about setting the authentication type,
see the OIDC configuration chapter.
Configuration
- Managing cryptographic storage and trusted certificates
- Setting token lifetimes
- Defining client authentication methods
oa_identity_provider
section of theWinCC OA config file. For a complete list of
options and their default values, see the oa_identity_provider
configuration section. User Management
User identities, roles, permissions, and groups are managed through the standard User administration. The identity provider uses this user administration for authentication and authorization.
Migration of Existing Projects
There is currently no automatic migration from previous authentication solutions to the internal identity provider. To use the identity provider, it is recommended to create a new project. In distributed system setups, all systems in the distributed configuration must use OIDC, mixed environments are not supported.
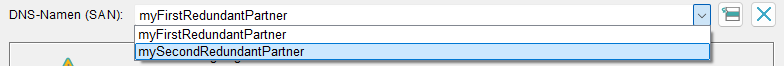
Redundant Projects
To use the OIDC provider within a redundant project it necessary to add both redundancy partners to your project certificates. This can be done during the creation of a project within the project wizard, see Settings for Certificates - Default:.