ISA/IEC-62443
ISA/IEC-62443 is a series of standards, technical reports, and related information that define procedures for implementing electronically secure Industrial Automation and Control Systems (IACS). This guidance applies tend-users (i.e., asset owners), system integrators, security practitioners, and control systems manufacturers responsible for manufacturing, designing, implementing, or managing IACS systems.
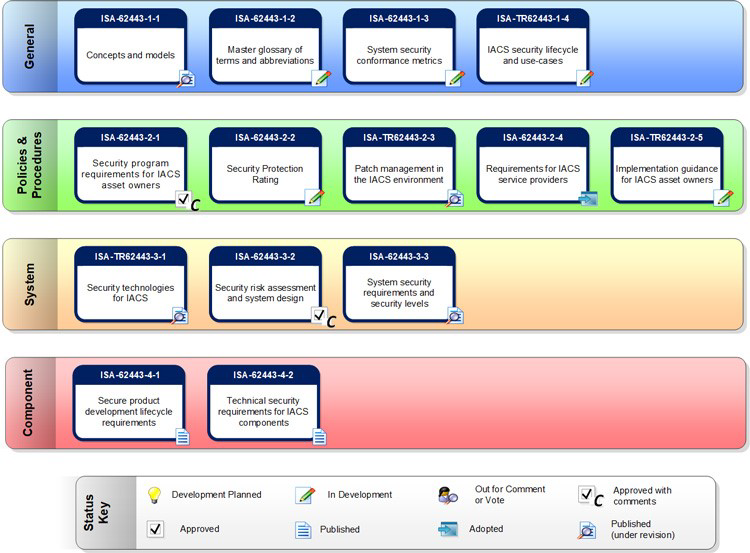
This standard has four different parts:
Part 1 (General)
Part 1 deals with general aspects and security standards. It defines an everyday basis in the form of terminology, concepts, and models for electronic security in industrial automation and process control systems. The following aspects are covered:
- Terminology
- Concepts
- Models
- Compliance metrics
- Security Levels (SL):
- SL 1 - Protection against casual or coincidental violation
- SL 2 - Protection against intentional violation using simple means
- SL 3 - Protection against intentional violation using sophisticated means
- SL 4 - Protection against intentional violation using sophisticated means with extended resources
Part 2 (Policies and Procedures)
Part 2 deals with implemented policies and procedures on-site and must be considered by the asset owner (see documents 2-1, 2-2, and 2-3). It supports the development of a program for the security of industrial automation and control systems. Besides, this part supplies comprehensive support related process activities and critical elements when developing a cybersecurity management system. This norm covers the following aspects:
- Organization
- Training/awareness
- Continuity plan
- Policies, procedures
- Personnel security
- Physical security
- Network segmentation
- Account administration
- Authentication
- Authorization
- Risk management and implementation
- Solution development and maintenance
- Incident planning and response
Part 3 (System)
Part 3 deals with the overall and network system and must be considered by the Integrator (see documents 3-2 and 3-3). It deals with implementing a security program in practical use during the conception and introduction phases. This security program also includes the definition and use of parameters for a valuable measurement of the program.
This norm covers the following aspects:
- System architecture, network segmentation
- Zones and conduits
- SL for systems
- FR 1 – Identification and authentication control
- FR 2 – Use control
- FR 3 – System integrity
- FR 4 – Data confidentiality
- FR 5 – Restricted data flow
- FR 6 – Timely response tevents
- FR 7 – Resource availability
Part 4 (Component)
Part 4 specifies industrial automation and process control systems' criteria where these systems differ from other IT systems from a security point of view. This part deals with requirements on components such as WinCC OA. ETM professional control GmbH holds a 4-1 certificate for the development process and a 4-2 certificate for WinCC OA. The mapping between the 4-2 certificate and the corresponding chapters within this Security Guideline is available in chapter Mapping tIEC 62443-4-2.
This norm covers the following aspects:
- Product development process
- PLCs
- HMI devices
- PC stations
- Firewalls
- Gateways
- Switches
- Functions
- Applications
- Data