Configuration of the Multiplexing Proxy
The proxy can be configured according to your project requirements. The Multiplexing Proxy can either be used as a normal manager in your project (default), as a remote Manager where multiple projects can be managed by one proxy. The proxy also supports redundant and distributed project configurations The following chapter describes how to set up the Multiplexing Proxy in different use cases.
Local host communication is never encrypted!
Following deployment scenarios and the necessary configuration files are described below:
- Multiplexing Proxy under Linux
- How to establish a Connection to a user-specific WinCC OA Server Manager via Multiplexing Proxy
- Multiplexing Proxy and IPV6 Addresses
Local Client and Proxy
If the WCCILproxy is deployed on the same host as WCCILdata (=DataManager) and the WCCILevent (=EventManager) no additional configuration for SSL is needed, because defaults are generated from the values of the config file entries [general] data and [general] event.
Single System Configuration
The Proxy and the Server are deployed on the same host. The Client (on a separate host) communicates with the Server via the Proxy.
- The client opens a connection to the Proxy and sends a message that tells the Proxy to open a connection to the DataManager.
- The Proxy opens a connection to the DataManager and links this connection to the connection to the client.
- The Proxy will send all messages received from the connection to the client to the DataManager and all messages received from the connection to the DataManager back to the client.
Opening the connection to the EventManager is done in the same way.

- 2 data and 2 alive connections to the DataManager
- 2 data and 2 alive connections to the EventManager
A client can open as many connections as needed. So, alive connections, not shown in the picture above, are tunneled via the Proxy too. In a ReduLAN configuration a client opens up to 8 connections:
Config File Entries
Server Configuration
No additional entries required.
Client Configuration
[general]
data="Server[:<dataPort>]"
event="Server[:<eventPort>]"
mxProxy="Server Server[:<proxyPort>] cert"If the mxProxy config was not specified, an automatic default entry will be used.
If you specified the mxProxy config entry manually, this will be used. Note that also the data and event entries are automatically set. Therefore, check that the server of your data and event entries matches the server of your manually specified mxProxy entry.
CAUTION! Note that although the mxProxy config entry would be set to "none", you must still start the Multiplexing Proxy in your project!
Remote Multiplexing Proxy
Often the Intranet of a company is considered secure and no communication encryption is required, but access from the Internet should be possible as well. There are many ways how an organization can expose its external-facing services to a larger and untrusted network, usually the Internet. A basic approach for this scenario is to simply place the Proxy behind a firewall into the DMZ.
The Multiplexing Proxy is no conventional manager and requires no DP-Identification. Therefore the config entries "data =" and "event =" inside the [general] section are not necessary for a remote proxy.
For such scenarios the default configuration is not possible, the Proxy and the client outside the company have to be configured manually.
Remote Multiplexing Proxy - Single Server
SSL is disabled on all the hosts running in the intranet ([general] mxProxy = “none”), only the client in the internet and the Proxy are using SSL.
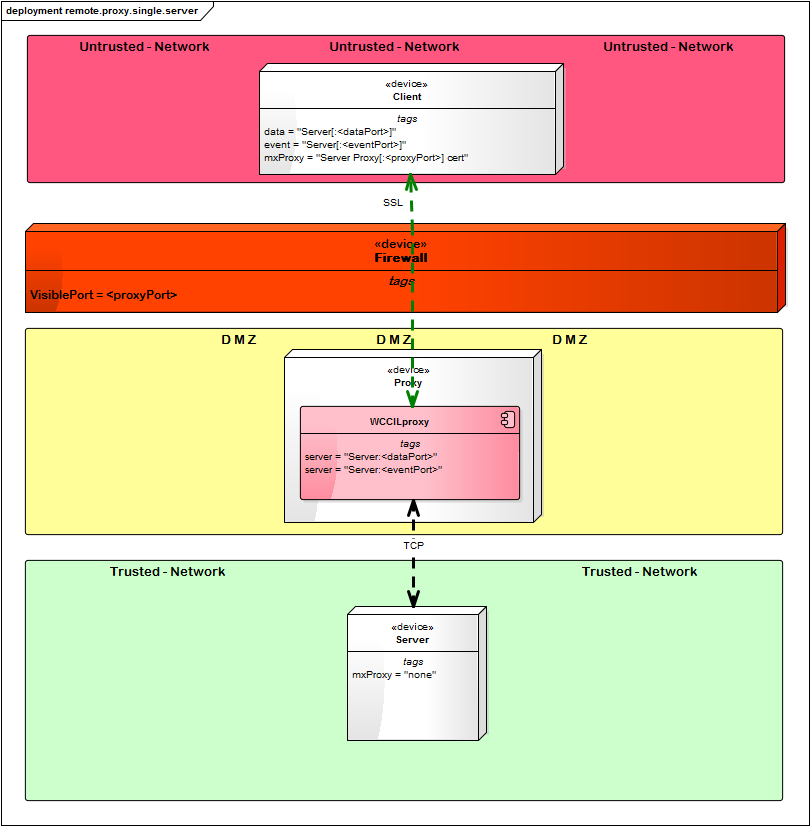
Config File Entries
Server Configuration
[general]
mxProxy="none"Remote Multiplexing Proxy Configuration
[proxy]
server="Server:<dataPort>"
server="Server:<eventPort>"The port numbers in the server configuration entries are mandatory even if the default port numbers are used for the DataManager and the EventManager.
Client Configuration
[general]
data="Server[:<dataPort>]"
event="Server[:<eventPort>]"
mxProxy="Server Proxy[:<proxyPort>] cert"The configuration of <dataPort>, <eventPort> and <proxyPort> in the data, event and mxProxy configuration entries are optional. If the default port numbers are used, <dataPort>, <eventPort> and <proxyPort> are not necessary.
Remote Multiplexing Proxy - Redundant Server
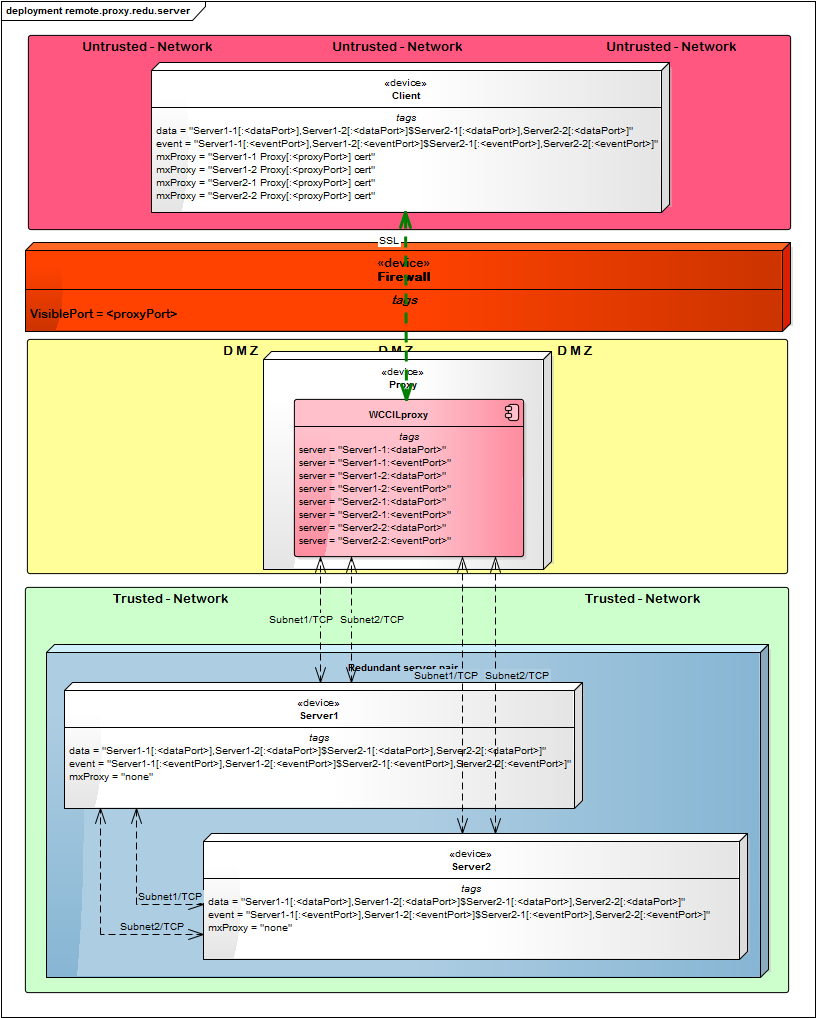
Redundant Server Pair Configuration
[general]
data="Server1-1[:<dataPort>],Server1-2[:<dataPort>]$Server2-1[:<dataPort>],Server2-2[:<dataPort>]"
event="Server1-1[:<eventPort>],Server1-2[:<eventPort>]$Server2-1[:<eventPort>],Server2-2[:<eventPort>]"
mxProxy="none"The configuration of <dataPort>, and <eventPort> in the data and event configuration entries are optional. If the default port numbers are used, <dataPort> and <eventPort> are optional.
Please note that the communication inside of the trusted network is not encrypted!
Remote Multiplexing Proxy Configuration
[proxy]
server = "Server1-1:<dataPort>"
server = "Server1-1:<eventPort>"
server = "Server1-2:<dataPort>"
server = "Server1-2:<eventPort>"
server="Server2-1:<dataPort>"
server="Server2-1:<eventPort>"
server="Server2-2:<dataPort>"
server="Server2-2:<eventPort>"The port numbers in the server configuration entries are mandatory even if the default port numbers are used for the DataManager and the EventManager.
Client Configuration
[general]
data="Server1-1[:<dataPort>],Server1-2[:<dataPort>]$Server2-1[:<dataPort>],Server2-2[:<dataPort>]"
event="Server1-1[:<eventPort>],Server1-2[:<eventPort>]$Server2-1[:<eventPort>],Server2-2[:<eventPort>]"
mxProxy = "Server1-1 Proxy[:<proxyPort>] cert"
mxProxy = "Server1-2 Proxy[:<proxyPort>] cert"
mxProxy = "Server2-1 Proxy[:<proxyPort>] cert"
mxProxy = "Server2-2 Proxy[:<proxyPort>] cert"The configuration of <dataPort>, <eventPort> and <proxyPort> in the data, event and mxProxy configuration entries are optional. If the default port numbers are used, <dataPort>, <eventPort> and <proxyPort> are not necessary.
Remote Multiplexing Proxy - Redundant Server And Redundant Proxy
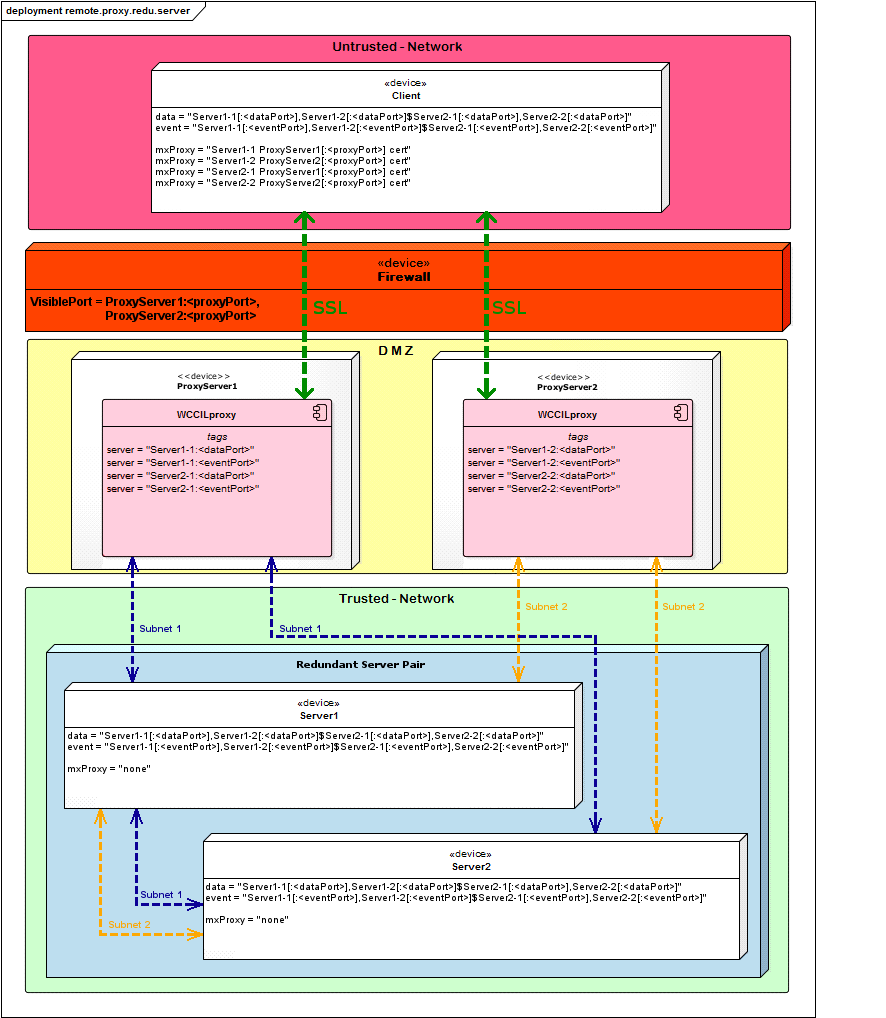
Redundant Server Pair Configuration
[general]
data="Server1-1[:<dataPort>],Server1-2[:<dataPort>]$Server2-1[:<dataPort>],Server2-2[:<dataPort>]"
event="Server1-1[:<eventPort>],Server1-2[:<eventPort>]$Server2-1[:<eventPort>],Server2-2[:<eventPort>]"
mxProxy="none"The configuration of <dataPort>, and <eventPort> in the data and event configuration entries are optional. If the default port numbers are used, <dataPort> and <eventPort> are not necessary.
Please note that the communication inside of the trusted network is not encrypted!
Remote Multiplexing Proxy Configuration 1
[proxy]
server = "Server1-1:<dataPort>"
#server = "Server1-2:<dataPort>"
server = "Server2-1:<dataPort>"
#server = "Server2-2:<dataPort>"
server = "Server1-1:<eventPort>"
#server = "Server1-2:<eventPort>"
server = "Server2-1:<eventPort>"
#server = "Server2-2:<eventPort>"[proxy]
#server = "Server1-1:<dataPort>"
server = "Server1-2:<dataPort>"
#server = "Server2-1:<dataPort>"
server = "Server2-2:<dataPort>"
#server = "Server1-1:<eventPort>"
server = "Server1-2:<eventPort>"
#server = "Server2-1:<eventPort>"
server = "Server2-2:<eventPort>"The port numbers in the server configuration entries are mandatory even if the default port numbers are used for the DataManager and the EventManager.
Client Configuration
Note that when you are using a mobile device or the Desktop UI, enter the necessary "Client Configuration" config entries described below into the config.webclient file.
[general]
data="Server1-1[:<dataPort>],Server1-2[:<dataPort>]$Server2-1[:<dataPort>],Server2-2[:<dataPort>]"
event="Server1-1[:<eventPort>],Server1-2[:<eventPort>]$Server2-1[:<eventPort>],Server2-2[:<eventPort>]"
mxProxy="Server1-1 Proxy-1[:<proxyPort>] cert"
mxProxy="Server1-2 Proxy-2[:<proxyPort>] cert"
mxProxy="Server2-1 Proxy-1[:<proxyPort>] cert"
mxProxy="Server2-2 Proxy-2[:<proxyPort>] cert"Multiplexing Proxy in a distributed System
For the configuration of the multiplexing proxy in a distributed system, you have to specify different config entries for the different systems. For an example see chapter Example on a Distributed System with different WinCC OA Versions.
How to establish a Connection to a user-specific WinCC OA Server Manager via Multiplexing Proxy
The WinCC OA multiplexing proxy establishes a connection to unblocked WinCC OA server managers. Some WinCC OA server Managers (Data Manager, Event Manager, Redu Manager, Split Manager) are unblocked by default.
The WCCILproxy can establish a connection since the proxy knows the default ports of the server or reads the changed port configuration from the config file. Since the WCCILproxy does not know how the client addresses the server, via host name or via IP address, the WCCILProxy generates not only a [proxy] server = entry per server but an entry for each host name and each IP address of the host.
For a host with 2 network interface cards, the WCCILproxy generates at least 5 [proxy]server = entries if redundant network is configured. An entry for the IP address of each network interface card.
server = "192.168.1.1:<dataPort>"
server = "192.168.2.1:<dataPort>"for example,
server = "speedy:<dataPort>"
server = "speedy_1:<dataPort>"
server = "speedy_2:<dataPort>"In order to speed up and facilitate the project work, WinCC OA offers the keyword $host. This keyword generates the necessary entries for the specific server (WinCC OA System). This entry informs the WCCILproxy that a customer-specific server exists and that it should create for this server the same defaults as for the managers unblocked by default,
In the following example for the server host "Speedy" with the server port 1234:
[proxy]
server = "$host:1234"
- an entry for each IP address of each network interface card:
e.g.
[proxy]
server = "192.168.1.1:1234"
server = "192.168.2.1:1234"
- an entry for each host name of each IP address
e.g.
[proxy]
server = "speedy:1234"
server = "speedy_1:1234"
server = "speedy_2:1234“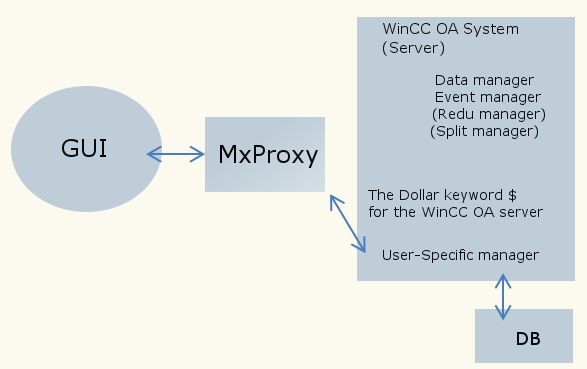
Multiplexing Proxy under Linux
When the multiplexing proxy is used under Linux, the maximum number of clients connected via multiplexing proxy simultaneously, is limited.
The maximum number of file descriptors per process is 1024. You can set the number of available file descriptors for a process by using the shell command ulimit -n <number of file descriptors>. These limits are always taken into account.
The number of file descriptors in the multiplexing proxy for a single client connection:
- if the clients use single network connections the number is 8. (1 connection requires 8 file descriptors)
- if the clients use redundant network connections the number is 16. (1 connection requires 16 file descriptors)
If the alive supervision is used, this may also have an impact on this number. There is a certain reserve ofthe available file descriptors in the multiplexing proxy for other purposes like log files, standard input/output, etc.
Some typical Client scenarios:
| Example 1 |
| The clients use single network connections |
| Alive supervision is on |
| The number of available file descriptors per process was set to 4096 via ulimit -n |
| The maximum number of clients connected via multiplexing proxy simultaneously, is 126. |
| Example 2 |
| The clients use redundant network connections |
| Alive supervision is on |
| The number of available file descriptors per process was set to 4096 via ulimit -n |
| The maximum number of clients connected via multiplexing proxy simultaneously, is 63. |
| Example 3 |
| The clients use single network connections |
| Alive supervision is on |
| The number of available file descriptors per process was set to 256 via ulimit -n |
| The maximum number of clients connected via multiplexing proxy simultaneously, is 30. |
Multiplexing Proxy and IPV6 Addresses
[general]
mxProxy = "[::1] [::1]:5678 cert"
[proxy]
server = "[fe80::2c5c:5415:98f1:82f3]:1234"