Secure Connection
The IEC 61850 client supports TLS encryption of communication between client and server. If TLS encryption is not supported by the server, this option must not be activated.
Certificates
The certificates used for encrypting the communication are server specific and must be saved in the project directory. By default they are saved in WinCC_OA_Proj\data\IEC61850\cert. With the config entry [iec61850]certPath a custom directory can be created in WinCC_OA_Proj\data\IEC61850\. e.g.: the entry [iec61850]certPath=“myCertifcates“ will create the directory WinCC_OA_Proj\data\IEC61850\ myCertifcates.
Certificates in the *.pem format are supported.
Password encryption
For all passwords mentioned below, that are saved in encrypted state on the internal datapoints the following applies: the encryption is done with a default certificate (driver_private.key), which is created in the course of the WinCC OA installation and placed in WinCC_OA_Proj/config.
Security Tab
The Security Tab shows the security relevant settings for the driver. With the exception
of the password, the settings applied here will be saved to the corresponding element on
the internal datapoint _IEC61850_IED in the structure .Config.Security.
See also the Description of
the internal datapoint.
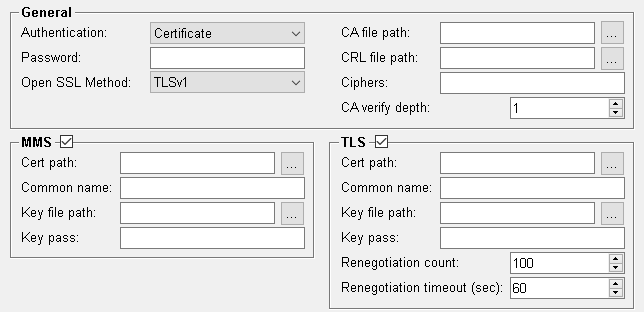
General
Authentication This sets the type of encryption. Available are:
- None: The communication is not encrypted.
- Password: The communication is not encrypted. The password will be saved encrypted on the internal datapoint, but sent as plain text.
- TLS + Password: The communication between client and server is encrypted using TLS. The use of a password is optional
Password This entry is optional. The password is saved encrypted on the internal datapoint
.Config/Password.
TLS Method
Sets the type of TLS encryption. This must match the encryption type used by the corresponding server. Available methods:
- TLSv1
- TLSv1.1
- SSLv2
- SSLv3
- SSLv2and3
CA file path
File containing the certificates of the Certificate Authority (CA certificates). Can be selected using the button next to the field.
CRL file path
The Revocation List of the Certification Authority. Can be selected using the button next to the field.
Ciphers
The openSSL Cipher Suite string. If the field is left empty, the following string is
used:
"TLSv1:TLSv1.1:TLSv1.2:SSLv3:!SSLv2:!aNULL:!eNULL:!CAMELLIA:!EXPORT40:!EXPORT56:@STRENGTH"
CA verify depth
The Depth of certificate chaining for Certificate Authority files. Allowed values are 0-99999.
MMS
Can be disabled to match device capabilities.
Cert path
The Certificate for the MMS encryption. Can be selected using the button next to the field.
Common name
The MMS common name. This will be expected by the server for received MMS certificates. The name will be saved in clear text on the internal datapoint.
Key file path
The Private Key for the MMS encryption. Can be selected using the button next to the field.
Key pass
The passphrase for decrypting the Private Key. Saved encrypted on the internal datapoint.
TLS
Can be disabled to match device capabilities.
Cert path
The Certificate for the TLS encryption. Can be selected using the button next to the field.
Common name
The TLS common name. This will be expected by the server for received TLS certificates. The name will be saved in plain text on the internal datapoint.
Key file path
The Private Key for the TLS encryption. Can be selected using the button next to the field.
Key pass
The passphrase for decrypting the Private Keys. Saved encrypted on the internal datapoint.
Renegotiation count
The maximum number of exchanged MMS messages, before the encryption of the connection is reverified.
Renegotiation timeout
The maximum time in seconds, before the encryption of the connection is reverified.